What is a DNS leak and why should I care?
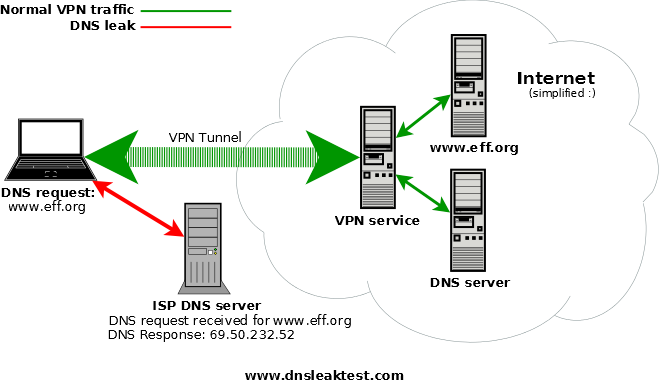
When using an anonymity or privacy service, it is extremely important that all traffic originating from your computer is routed through the anonymity network. If any traffic leaks outside of the secure connection to the network, any adversary monitoring your traffic will be able to log your activity.
DNS or the domain name system is used to translate domain names such as www.privacyinternational.org into numerical IP addresses e.g. 123.123.123.123 which are required to route packets of data on the Internet. Whenever your computer needs to contact a server on the Internet, such as when you enter a URL into your browser, your computer contacts a DNS server and requests the IP address. Most Internet service providers assign their customers a DNS server which they control and use for logging and recording your Internet activities.
Under certain conditions, even when connected to the anonymity network, the operating system will continue to use its default DNS servers instead of the anonymous DNS servers assigned to your computer by the anonymity network. DNS leaks are a major privacy threat since the anonymity network may be providing a false sense of security while private data is leaking.
Modern web browsers support encrypted DNS, like DNS-over-HTTPS, and this feature is often enabled by default. This is beneficial to prevent leaks to the ISP or an adversary with access to local traffic, like on a public Wi-Fi network, because the DNS queries are wrapped in encryption between the local device and the DNS server. It is important to note that the web browser's default secure DNS provider might not be desirable from a privacy standpoint (i.e. logging policies) and queries sent to the secure DNS provider could be considered to be a leak.
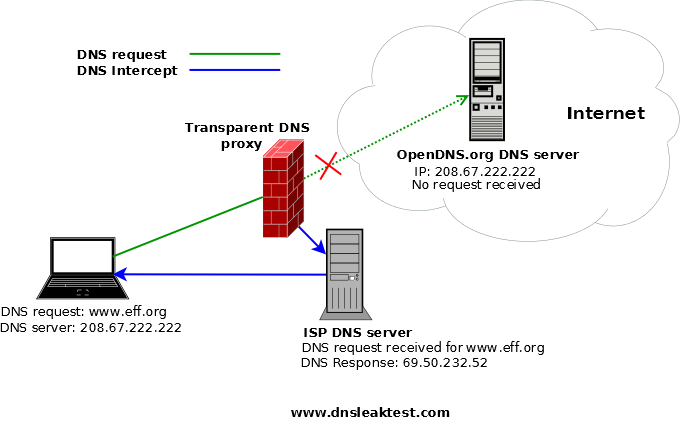
Transparent DNS proxies
Some ISP's are now using a technology called 'Transparent DNS proxy'. Using this technology, they will intercept all DNS lookup requests (TCP/UDP port 53) and transparently proxy the results. This effectively forces you to use their DNS service for all DNS lookups.
If you have changed your DNS settings to use an 'open' DNS service such as Google, Comodo or OpenDNS, expecting that your DNS traffic is no longer being sent to your ISP's DNS server, you may be surprised to find out that they are using transparent DNS proxying. You can easily test this by clicking on the dns leak test button on the homepage.
If your ISP implements a transparent DNS proxy it is very important that you use one of the methods on the dns leak fix page to ensure that when you are connected to the VPN, there is no chance of your requests being intercepted.